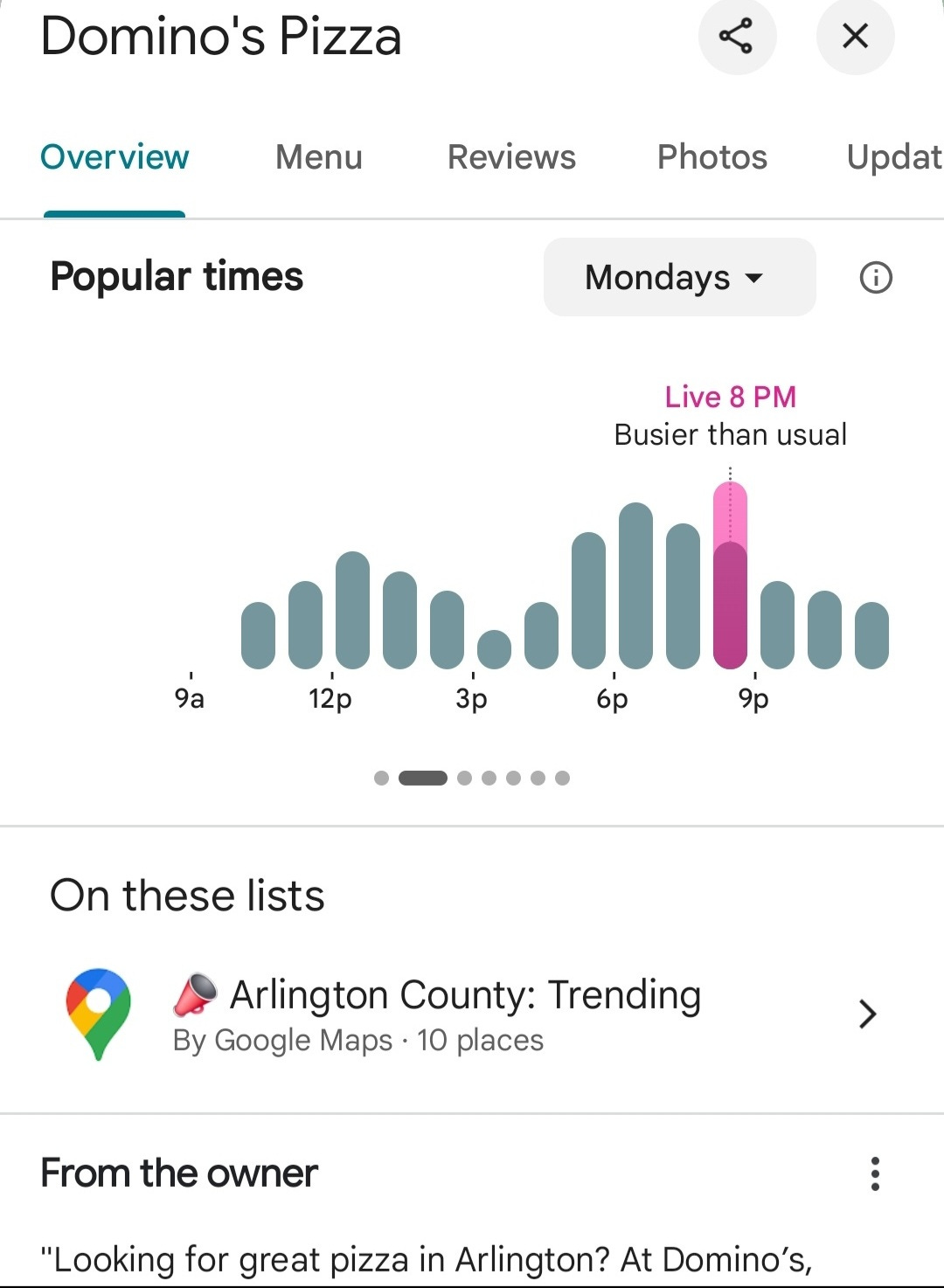
BLUF: Surges in Google review data, such as the example shown below from Domino’s Pizza, may appear trivial. But when aggregated and interpreted through an OSINT (Open-Source Intelligence) lens, they can offer surprising insights into national security activity. This article explores one such trend - the so-called "Pentagon Pizza Report" - and its wider implications.
A Slice of the Action: What the Data Shows
Social media users on X (formerly Twitter) have been posting what they dub the "Pentagon Pizza Report" - screenshots showing sudden spikes in Google activity and reviews for late-night food spots near the Pentagon. One popular example, seen above, displays a live surge in customer activity at 8 PM on a Monday. At first glance, this seems like standard consumer behaviour. But to trained analysts, patterns like this can signal unusual movement - night shifts, emergency taskings, or surge deployments among defence and intelligence personnel.
By tracking these public data signals over time, analysts can build a picture of when something is “off-pattern.” For example, a sustained spike in food orders and reviews near a sensitive installation late at night might coincide with covert planning sessions, snap deployments, or crisis response activity. It’s not definitive - but it’s a tell. And in intelligence, tells matter.
AdTech and Surveillance: The Chinese Playbook
This kind of OSINT analysis is not new, nor is it solely the domain of hobbyists online. According to a Wall Street Journal investigation, Chinese intelligence operatives used advertising data purchased from U.S. ad exchanges to monitor mobile advertising identifiers (MAIDs). One use-case? Tracing travel patterns between the Pentagon and Washington, D.C.’s gay nightlife spots to identify potential targets for kompromat and blackmail.
A separate Brookings report detailed how Chinese data brokers exploited legal but under-regulated advertising networks to track movements of U.S. government personnel - not through espionage, but through clicks, proximity-based mobile ad tracking, and digital breadcrumbs we all leave behind.
These examples show the power of ambient digital intelligence: no hacking required, just careful analysis of open data. When a pizza joint near the Pentagon lights up with five-star reviews at odd hours, it may not be accidental.
Seeing the Signal in the Noise
OSINT practitioners are trained to observe patterns and outliers - what changes, when, and why. Could a sudden spike in late-night Uber drop-offs, a surge in LinkedIn activity in a niche industry, or a series of low-star restaurant reviews near a classified site be meaningful? In isolation, maybe not. In context, maybe critical.
The Pentagon Pizza Report is a reminder that the open web is brimming with tells - you just need to know where to look.
Challenge to Analysts and Enthusiasts
What other signals are hiding in plain sight? As open-source data becomes richer, so too does the threat surface. Think like a threat actor, and you’ll start to see the indicators and warnings that others miss. For those building threat intelligence capabilities or sharpening their analytic edge - this is your open challenge: identify, interpret, and share your own OSINT tells.
Tag your findings with #OSTimes. The next pattern might be just a pizza order away.
If you'd like a follow-up piece with interactive examples, toolkits for tracking live OSINT trends, or training on recognising threat indicators from public data, leave a comment below or subscribe for updates.